In an era where news of data breaches and cyber threats is all too common, it’s imperative to focus on robust cybersecurity measures. Today, we’ll delve into the essentials of implementing a cybersecurity strategy from scratch, guided by the NIST Cybersecurity Framework (CSF).
Understanding the NIST Cybersecurity Framework
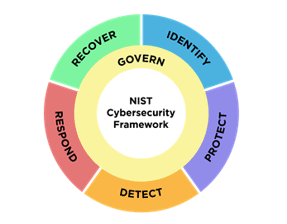
The NIST Cybersecurity Framework is a comprehensive guide designed to help organizations manage and reduce cybersecurity risk. It consists of five main functions, each critical to building a robust cybersecurity strategy:
- Identify: This function involves understanding and managing cybersecurity risks to systems, assets, data, and capabilities. It’s the foundational step that sets the stage for the other functions.
- Protect: The Protect function encompasses safeguards to ensure the safe delivery of critical services. This includes access control, data security, and maintenance processes.
- Detect: This function focuses on identifying cybersecurity events promptly. Implementing continuous monitoring solutions helps in early detection of potential breaches.
- Respond: In the event of a cybersecurity incident, the Respond function includes the necessary actions to address and manage the impact. It involves incident response planning, communication, and analysis.
- Recover: The Recover function supports timely recovery to normal operations after a cybersecurity event. This includes planning for resilience and restoring capabilities or services that were impaired.
Embarking on a Cybersecurity Journey
Launching a cybersecurity strategy can be a daunting task. Thankfully, the NIST CSF offers a structured approach to help organizations navigate this complex terrain. According to the framework, the first and most critical control to implement is the Identify function.
Why Start with Identify?
The Identify function serves as the cornerstone of a sound cybersecurity strategy. It empowers organizations to gain a comprehensive understanding of their environment, encompassing assets, data, and risks. By establishing a thorough grasp of what needs protection, companies can effectively prioritize their cybersecurity efforts.
Key Steps in the Identify Function
- Asset Management: This involves inventorying all physical and digital assets. A detailed inventory helps organizations know what they have, where it’s located, and its importance.
- Business Environment: Understanding the organization’s role in the supply chain and the broader business context is crucial. This insight helps in identifying potential threats and vulnerabilities.
- Governance: Establishing policies, procedures, and governance structures ensures a consistent approach to cybersecurity across the organization.
- Risk Assessment: Identifying and evaluating risks helps organizations understand potential threats and their impact. This step is vital for effective risk management.
- Risk Management Strategy: Defining risk tolerance and mitigation strategies allows organizations to prioritize actions and allocate resources efficiently.
Asset Management: The Heart of Identify
Among these key steps, Asset Management stands out as particularly critical. It involves creating a comprehensive inventory of all hardware, software, data, and other assets, understanding their role and importance, and identifying ownership and responsibility for each asset. This process is foundational because:
- Visibility: Knowing what assets exist and their significance helps in prioritizing security efforts.
- Ownership and Responsibility: Clear identification of who owns and is responsible for each asset ensures accountability.
- Risk Prioritization: By understanding asset importance, organizations can better protect critical assets and allocate resources more effectively.
Aligning with Business Objectives
Starting with the Identify function ensures that subsequent controls are grounded in a solid understanding of the organization’s unique context and needs. This approach not only enhances security but also aligns with business objectives, providing a balanced and effective cybersecurity strategy.
Conclusion
In conclusion, as we navigate an increasingly digital world, cybersecurity becomes more crucial than ever. Embarking on this journey with the NIST Cybersecurity Framework and beginning with the Identify function lays a solid foundation for a robust and resilient cybersecurity strategy. By understanding and managing assets, organizations can better protect themselves against ever-evolving cyber threats.


0 Comments